
Introduction
This switch really is a Swiss Army knife — but like any multi-tool, it has its quirks. The blade isn’t the longest, it doesn’t do everything perfectly, but it gets the job done and it’s tough. I’ve used these for years now, and they still surprise me with how hardy they are.
In this guide we’ll go through some of the snags I’ve hit and the solutions I’ve found. One major requirement for me was limiting MAC addresses per port, and this little Swiss Army knife can do it!
The diagram!
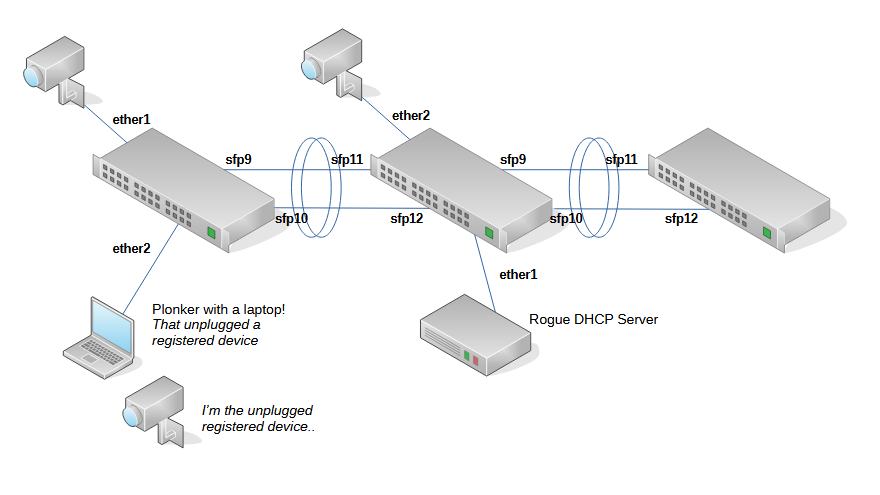
The very basic we can do
Basic Configuration
A simple starting point to limit MACs per port:
/interface ethernet switch port
set 0 learn-limit=1 vlan-type=edge-port
set 1 learn-limit=1 vlan-type=edge-port
set 2 learn-limit=1 vlan-type=edge-port
set 3 learn-limit=1 vlan-type=edge-port
set 4 learn-limit=1 vlan-type=edge-port
set 5 learn-limit=1 vlan-type=edge-port
set 6 learn-limit=1 vlan-type=edge-port
set 7 learn-limit=1 vlan-type=edge-portThis trick stops the switch from learning more than the configured number of MAC addresses per port. It’s not foolproof — after a reboot, the switch will learn whichever device connects first — but it’s a start.
Adding More Controls
To harden things further:
/interface ethernet switch port
set 0 isolation-leakage-profile-override=2 learn-limit=1 vlan-type=edge-port
set 1 isolation-leakage-profile-override=2 learn-limit=1 vlan-type=edge-port
set 2 isolation-leakage-profile-override=2 learn-limit=1 vlan-type=edge-port
set 3 isolation-leakage-profile-override=2 learn-limit=1 vlan-type=edge-port
set 4 isolation-leakage-profile-override=2 learn-limit=1 vlan-type=edge-port
set 5 isolation-leakage-profile-override=2 learn-limit=1 vlan-type=edge-port
isolation-leakage-profile-override=2→ drops unwanted DHCP traffic coming in from client ports.learn-limit=1→ limits each edge port to one learned MAC.vlan-type=edge-port→ explicitly tells the switch this is an edge port.
DHCP Spoofing Protection
To stop rogue DHCP servers:
/interface ethernet switch port-isolation
add forwarding-type=bridged port-profile=2 ports=trunk1,trunk2,sfp9,sfp10,sfp11,sfp12 protocol-type=dhcpv4 type=dst
add forwarding-type=bridged port-profile=2 ports=trunk1,trunk2,sfp9,sfp10,sfp11,sfp12 protocol-type=dhcpv6 type=dstThis ensures DHCP traffic is only accepted from the trusted trunk ports (trunk1,trunk2,sfp9,sfp10,sfp11,sfp12).
Extras
- Port Flooding Protection → already built in with
learn-limitandunknown-unicast-flood=no. - Blackhole Ports → you can dump unused ports into a VLAN that doesn’t leave the switch (e.g. VLAN 999) to silently discard traffic. Example:
/interface ethernet switch vlan add ports=ether7,ether8 vlan-id=999 /interface ethernet switch ingress-vlan-translation add customer-vid=0 new-customer-vid=999 ports=ether7,ether8(Not included in the main config so you still have an emergency access port.)
Scope of this Test
- Requirement 1: Block unknown MAC addresses.
- Requirement 2: Block rogue DHCP servers.
This config isolates edge ports, limits learned MACs, and controls DHCP flooding.
Issues Encountered
- Unicast FDB (Forwarding Database) oddities
- Sometimes static entries wouldn’t apply until a reboot.
- With
svl=yes, things mostly worked after flushing the FDB, but withoutsvl=yesconnectivity would break. more testing is required if just rebooting the switch after making changes has an effect. - Lesson: CRS112’s FDB can be flaky — expect some trial and error.
- Trunks between two CRS112s
- At first, MACs learned on
trunk1were incorrectly appearing as learned ontrunk2, breaking DHCP relay. - After configuration cleanup and reboots, things stabilized, but this shows the quirks of the hardware. In a production environment where you may have to replace equipment fairly regularly this could be a deal breaker using this type of port level protection.
- At first, MACs learned on
The full configuration as it stands (for testing)
/interface bridge
add admin-mac=D4:01:C3:5D:CC:E6 auto-mac=no name=bridge1 protocol-mode=none
/interface vlan
add interface=bridge1 name=vlan100 vlan-id=100
/interface ethernet switch trunk
add member-ports=sfp11,sfp12 name=trunk2
add member-ports=sfp9,sfp10 name=trunk1
/interface wireless security-profiles
set [ find default=yes ] supplicant-identity=MikroTik
/interface bridge port
add auto-isolate=yes bpdu-guard=yes bridge=bridge1 edge=yes interface=ether1 learn=no unknown-unicast-flood=no
add auto-isolate=yes bpdu-guard=yes bridge=bridge1 edge=yes interface=ether2 learn=no unknown-unicast-flood=no
add auto-isolate=yes bpdu-guard=yes bridge=bridge1 edge=yes interface=ether3 learn=no unknown-unicast-flood=no
add auto-isolate=yes bpdu-guard=yes bridge=bridge1 edge=yes interface=ether4 learn=no unknown-unicast-flood=no
add auto-isolate=yes bpdu-guard=yes bridge=bridge1 edge=yes interface=ether5 learn=no unknown-unicast-flood=no
add auto-isolate=yes bpdu-guard=yes bridge=bridge1 edge=yes interface=ether6 learn=no unknown-unicast-flood=no
add bridge=bridge1 interface=sfp9 trusted=yes
add bridge=bridge1 interface=sfp10 trusted=yes
add bridge=bridge1 interface=sfp11 trusted=yes
add bridge=bridge1 interface=sfp12 trusted=yes
add auto-isolate=yes bpdu-guard=yes bridge=bridge1 edge=yes interface=ether7 learn=no unknown-unicast-flood=no
/interface ethernet switch acl
add action=drop src-mac-addr-state=sa-not-found src-ports=ether1,ether2,ether3,ether4,ether5,ether6 table=egress
add action=drop src-mac-addr-state=static-station-move src-ports=ether1,ether2,ether3,ether4,ether5,ether6 table=egress
/interface ethernet switch egress-vlan-tag
add tagged-ports=trunk2,trunk1,switch1-cpu vlan-id=100
add tagged-ports=trunk2,trunk1 vlan-id=400
add tagged-ports=trunk2,trunk1 vlan-id=401
add tagged-ports=trunk2,trunk1 vlan-id=1000
/interface ethernet switch ingress-vlan-translation
add customer-vid=0 new-customer-vid=401 ports=ether1,ether2,ether3,ether4,ether5,ether6
/interface ethernet switch port
set 0 isolation-leakage-profile-override=2 learn-limit=1 vlan-type=edge-port
set 1 isolation-leakage-profile-override=2 learn-limit=1 vlan-type=edge-port
set 2 isolation-leakage-profile-override=2 learn-limit=1 vlan-type=edge-port
set 3 isolation-leakage-profile-override=2 learn-limit=1 vlan-type=edge-port
set 4 isolation-leakage-profile-override=2 learn-limit=1 vlan-type=edge-port
set 5 isolation-leakage-profile-override=2 learn-limit=1 vlan-type=edge-port
/interface ethernet switch port-isolation
add forwarding-type=bridged port-profile=2 ports=trunk1,trunk2,sfp9,sfp10,sfp11,sfp12 protocol-type=dhcpv4 registration-status="" traffic-type="" type=dst
add forwarding-type=bridged port-profile=2 ports=trunk1,trunk2,sfp9,sfp10,sfp11,sfp12 protocol-type=dhcpv6 registration-status="" traffic-type="" type=dst
/interface ethernet switch unicast-fdb
add mac-address=F4:1E:57:41:04:47 port=ether1 svl=yes
add mac-address=F4:1E:57:41:04:B2 port=ether2 svl=yes
/interface ethernet switch vlan
add ports=trunk2,trunk1,ether1,ether2,ether3,ether4,ether5,ether6 svl=yes vlan-id=401
add ports=trunk2,trunk1,switch1-cpu svl=yes vlan-id=100
add ports=trunk2,trunk1 svl=yes vlan-id=400
add ports=trunk2,trunk1 svl=yes vlan-id=1000
/ip address
add address=192.168.88.1/24 comment=defconf network=192.168.88.0
/ip dhcp-client
add disabled=no interface=vlan100
/system clock
set time-zone-name=Europe/London
/system identity
set name=test-sw01
/tool romon
set enabled=yesConclusion
The CRS112 is indeed a Swiss Army knife — not perfect, but versatile. With the right config you can:
- Limit MACs per port.
- Block rogue DHCP.
- Isolate clients.
- Contain traffic floods.
It takes patience (the Unicast FDB in particular can be frustrating), but once tuned, these little switches can do a lot more than you’d expect for their size and price.
and there’s more!
Storm Control (Broadcast/Multicast limit)
Prevents a single misbehaving device from flooding the switch with broadcasts or multicasts:
/interface ethernet switch port
set ether1 ingress-rate=1000kbps broadcast-unknown-unicast-limit=100kbps multicast-limit=100kbpsSyslog / Remote Logging
Send logs to a central syslog server:
/system logging action
add name=remote target=remote remote=192.168.21.50
/system logging
add action=remote topics=dhcp
add action=remote topics=systemNetwatch or Scripted Alerts
Monitor upstream connectivity and alert/reboot if it goes down:
/tool netwatch
add host=8.8.8.8 interval=30s up-script="" down-script="/log warning \"WAN down!\""Safe Mode Habit
When testing configs, always use /system/console/safe-mode so if you misconfigure VLANs or isolation, the switch will revert after disconnect. (Not a config line, but worth mentioning in your guide!)
